Pegasus: Spyware sold to governments ‘targets activists’

Rights activists, journalists and lawyers around the world have been targeted with phone malware sold to authoritarian governments by an Israeli surveillance firm, media reports say.
They are on a list of some 50,000 phone numbers of people believed to be of interest to clients of the company, NSO Group, leaked to major news outlets.
It was not clear where the list came from - or how many phones had actually been hacked.
NSO denies any wrongdoing.
It says the software is intended for use against criminals and terrorists and is made available only to military, law enforcement and intelligence agencies from countries with good human rights records.
It said the original investigation which led to the reports, by Paris-based NGO Forbidden Stories and the human rights group Amnesty International, was “full of wrong assumptions and uncorroborated theories”.
But it added that it would “continue to investigate all credible claims of misuse and take appropriate action”.
The allegations about use of the software, known as Pegasus, were carried on Sunday by the Washington Post, the Guardian, Le Monde and 14 other media organisations around the world.
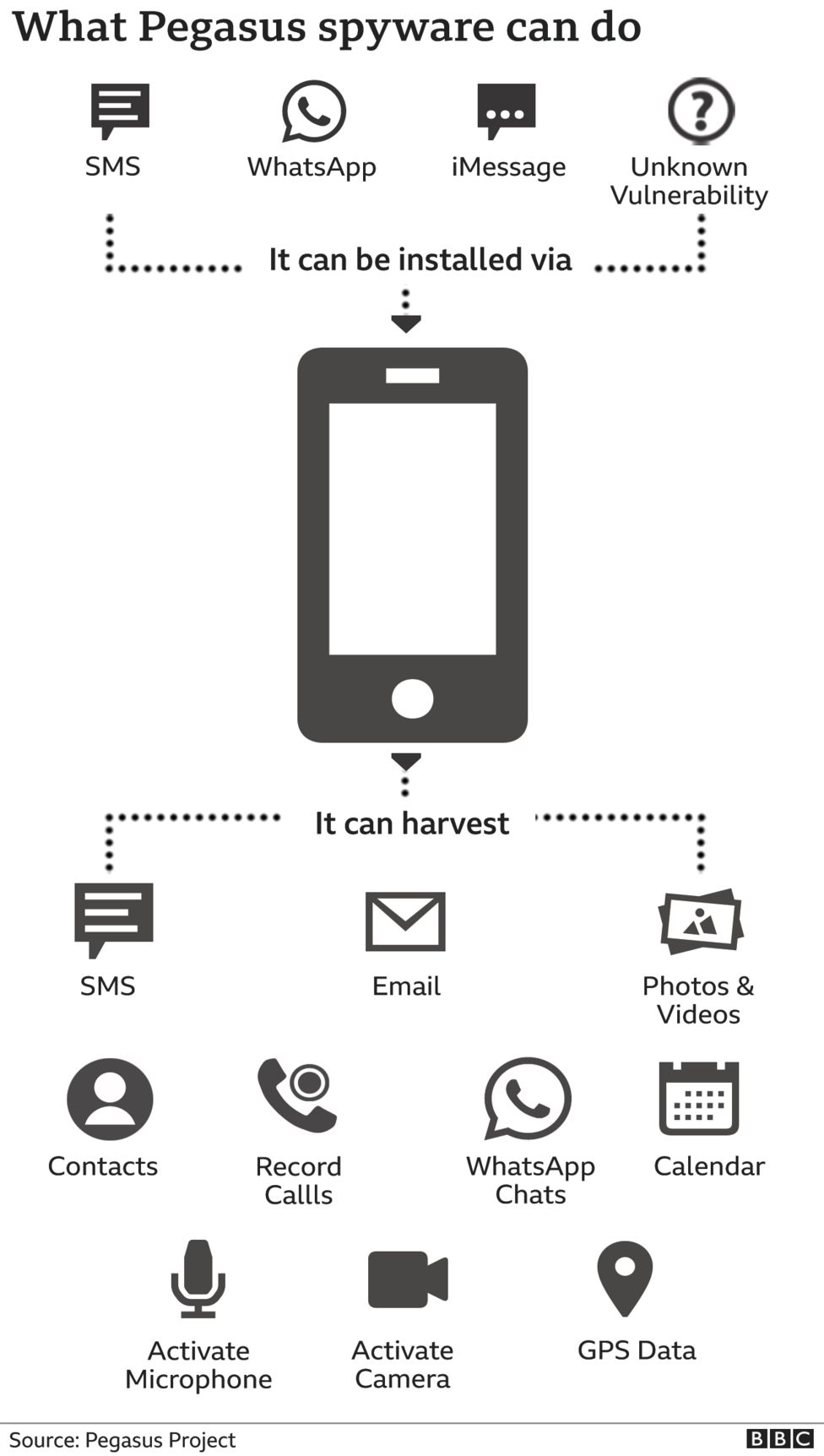
Pegasus infects iPhones and Android devices, allowing operators to extract messages, photos and emails, record calls and secretly activate microphones and cameras.
What do we know about the people targeted?
Media outlets working on the investigation said they had identified more than 1,000 people spanning over 50 countries whose numbers were on the list.
They include politicians and heads of state, business executives, activists, and several Arab royal family members. More than 180 journalists were also found to be on the list, from organisations including CNN, the New York Times and Al Jazeera.
Many of the numbers were clustered in 10 countries: Azerbaijan, Bahrain, Hungary, India, Kazakhstan, Mexico, Morocco, Rwanda, Saudi Arabia and the United Arab Emirates, according to the reports.
When contacted by the outlets involved in the investigation, spokespeople for these countries either denied that Pegasus was used or denied that they had abused their powers of surveillance.
It was not clear how many of the devices on the list had actually been targeted, but forensic analysis of 37 of the phones showed there had been “attempted and successful” hacks, the Washington Post reported.
This included people close to Saudi journalist Jamal Khashoggi, who was murdered in October 2018 while visiting the Saudi consulate in Istanbul, Turkey. His body was then dismembered.
The investigation found that spyware was installed on his fiancée’s phone days after his murder, and that his wife’s phone was targeted with spyware between September 2017 and April 2018.
The NSO Group said its technology was “not associated in any way with the heinous murder”.
The phone of Mexican journalist Cecilio Pineda Birto also appeared twice on the list, including in the month before he was murdered, the investigation found.
His phone disappeared from the scene of the murder so a forensic examination was not possible. NSO said that even if his phone was targeted, that did not mean that data collected was connected with his murder.

The phones of two Hungarian investigative journalists, Andras Szabo and Szabolcs Panyi, were found to have been successfully infected with the spyware.
Mr Panyi told Forbidden stories that learning of the hack was “devastating”.
“There are some people in this country who consider a regular journalist as dangerous as someone suspected of terrorism,” he said.
The Hungarian government was “not aware of any alleged data collection”, a spokesperson told the Guardian.
In India, more than 40 journalists, three opposition leaders and two ministers in Prime Minister Narendra Modi’s government were reported to be on the list.
This included the key opposition figure Rahul Gandhi, with two mobile phone numbers belonging to him found in the list. Mr Gandhi no longer has the devices so it was not possible to analyse them to determine if he had been hacked.
India’s government has denied using unauthorised surveillance.
This tool tells you if NSO’s Pegasus spyware targeted your phone

Over the weekend, an international consortium of news outlets reported that several authoritarian governments — including Mexico, Morocco and the United Arab Emirates — used spyware developed by NSO Group to hack into the phones of thousands of their most vocal critics, including journalists, activists, politicians and business executives.
A leaked list of 50,000 phone numbers of potential surveillance targets was obtained by Paris-based journalism nonprofit Forbidden Stories and Amnesty International and shared with the reporting consortium, including The Washington Post and The Guardian. Researchers analyzed the phones of dozens of victims to confirm they were targeted by the NSO’s Pegasus spyware, which can access all of the data on a person’s phone. The reports also confirm new details of the government customers themselves, which NSO Group closely guards. Hungary, a member of the European Union where privacy from surveillance is supposed to be a fundamental right for its 500 million residents, is named as an NSO customer.
The reporting shows for the first time how many individuals are likely targets of NSO’s intrusive device-level surveillance. Previous reporting had put the number of known victims in the hundreds or more than a thousand.
NSO Group sharply rejected the claims. NSO has long said that it doesn’t know who its customers target, which it reiterated in a statement to TechCrunch on Monday.
Researchers at Amnesty, whose work was reviewed by the Citizen Lab at the University of Toronto, found that NSO can deliver Pegasus by sending a victim a link which when opened infects the phone, or silently and without any interaction at all through a “zero-click” exploit, which takes advantage of vulnerabilities in the iPhone’s software. Citizen Lab researcher Bill Marczak said in a tweet that NSO’s zero-clicks worked on iOS 14.6, which until today was the most up-to-date version.
Amnesty’s researchers showed their work by publishing meticulously detailed technical notes and a toolkit that they said may help others identify if their phones have been targeted by Pegasus.
The Mobile Verification Toolkit, or MVT, works on both iPhones and Android devices, but slightly differently. Amnesty said that more forensic traces were found on iPhones than Android devices, which makes it easier to detect on iPhones. MVT will let you take an entire iPhone backup (or a full system dump if you jailbreak your phone) and feed in for any indicators of compromise (IOCs) known to be used by NSO to deliver Pegasus, such as domain names used in NSO’s infrastructure that might be sent by text message or email. If you have an encrypted iPhone backup, you can also use MVT to decrypt your backup without having to make a whole new copy.
The toolkit works on the command line, so it’s not a refined and polished user experience and requires some basic knowledge of how to navigate the terminal. We got it working in about 10 minutes, plus the time to create a fresh backup of an iPhone, which you will want to do if you want to check up to the hour. To get the toolkit ready to scan your phone for signs of Pegasus, you’ll need to feed in Amnesty’s IOCs, which it has on its GitHub page. Any time the indicators of compromise file updates, download and use an up-to-date copy.
Once you set off the process, the toolkit scans your iPhone backup file for any evidence of compromise. The process took about a minute or two to run and spit out several files in a folder with the results of the scan. If the toolkit finds a possible compromise, it will say so in the outputted files. In our case, we got one “detection,” which turned out to be a false positive and has been removed from the IOCs after we checked with the Amnesty researchers. A new scan using the updated IOCs returned no signs of compromise.
Given it’s more difficult to detect an Android infection, MVT takes a similar but simpler approach by scanning your Android device backup for text messages with links to domains known to be used by NSO. The toolkit also lets you scan for potentially malicious applications installed on your device.
The toolkit is — as command line tools go — relatively simple to use, though the project is open source so it won’t be long before someone will surely build a user interface for it. The project’s detailed documentation will help you — as it did us.
What the latest Pegasus spyware leaks tell us

The reports from the Guardian, the Washington Post, and 15 other media organizations are based on a leak of tens of thousands of phone numbers that appear to have been targeted by Pegasus. While the devices associated with the numbers on the list were not necessarily infected with the spyware, the outlets were able to use the data to establish that journalists and activists in many countries were targeted—and in some cases successfully hacked.
The leaks indicate the scope of what cybersecurity reporters and experts have said for years: that while NSO Group claims its spyware is designed to target criminals and terrorists, its actual applications are much more broad. (The company released a statement in response to the investigation, denying that its data was leaked, and that any of the resulting reporting was true.)
My colleague Patrick Howell O’Neill has been reporting for some time on claims against NSO Group, which “has been linked to cases including the murder of Saudi journalist Jamal Khashoggi, the targeting of scientists and campaigners pushing for political reform in Mexico, and Spanish government surveillance of Catalan separatist politicians,” he wrote in August 2020. In the past, NSO has denied these accusations, but it has also more broadly argued that it can’t be held responsible if governments misuse the technology it sells them.
The company’s central argument, we wrote at the time, is one “that is common among weapons manufacturers.” Namely: “The company is the creator of a technology that governments use, but it doesn’t attack anyone itself, so it can’t be held responsible.”
線上諮詢
與我們合作,馬上展開全新的創作里程碑
- 📅 立即預約,30 秒完成!
- 🎯 與創辦人 1 對 1 交流,獲得專屬建議! 🎯 與創辦人 1 對 1 交流!